This has been a really busy ransomware week. In addition to lots of crapware released, we also saw an EDA2 branch called Stolich that is only going to lead to more skidware being released. We also saw a new codebase actively being used to pump out small ransomware infections, which like HiddenTear and EDA2, is just going to become a pain to keep up with.
The big news was the POC for a UEFI Ransomware presented at BlackHat Asia, Matrix Ransomware being distributed by RIG and having worm characteristics, and the joke ransomware called RensenWare that required a victim to get a very high score in a game to get a decryption key.
Contributors and those who provided new ransomware information and stories this week include: @BleepinComputer, @malwrhunterteam, @PolarToffee, @fwosar, @struppigel, @demonslay335, @malwareforme, @jorntvdw, @FourOctets, @DanielGallagher , @campuscodi, @JAMESWT_MHT, @Seifreed, @emsisoft, @malware_traffic, @cylanceinc, @sans_isc, and @F5Labs.
If you are interested in ransomware or InfoSec, I suggest you follow them on Twitter.
April 1st 2017
Gigabyte Firmware Flaws Allow the Installation of UEFI Ransomware
At the BlackHat Asia 2017 security conference, researchers from cyber-security firm Cylance disclosed two vulnerabilities in the firmware of Gigabyte BRIX small computing devices, which allow an attacker to write malicious content to the UEFI firmware.

April 2nd 2017
GX40 Ransomware Discovered
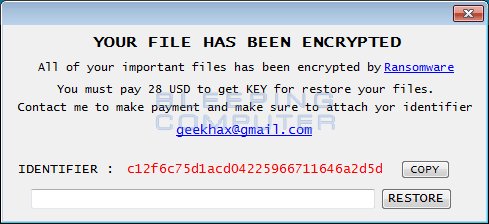
BleepingComputer discovered the new in-dev GX40 Ransomware, which appears to be a new codebase that is used to push out ransomware infections. Add the .encrypted extension to encrypted files and has a payment email gx40@yahoo.com.
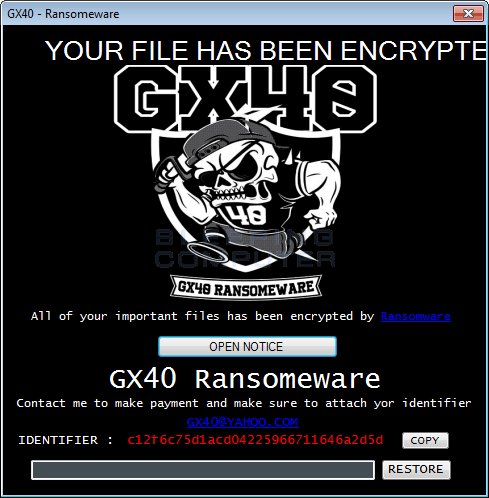
Another GX40 Based Ransomware Discovered
BleepingComputer discovered another ransomware from the same codebase as GX40. This one uses geekhax@yahoo.com as the contact email.
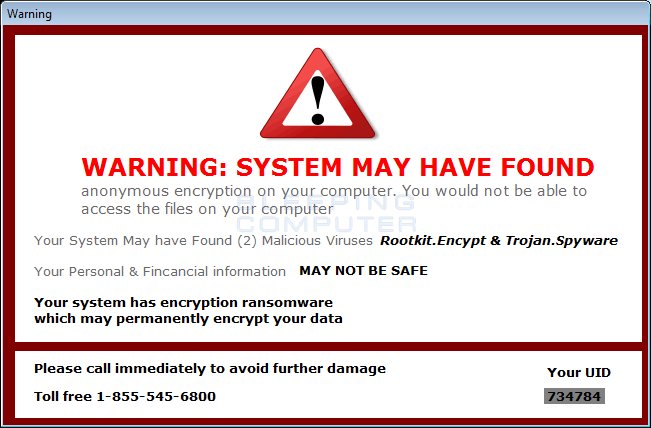
AngryKite Ransomware Discovered
A new variant of the Krider ransomware called AngryKite was discovered by BleepingComputer. AngryKite randomizes filename and appends the .NumberDot extension to encrypted files. Wants you to call 855-455-6800 for help. May be decryptable.
DeathNote Hackers Ransomware Discovered
DeathNote Hackers ransomware discovered by Michael Gillespie. Already handled by StupidDecrypter an can also be unlocked by entering the code 83KYG9NW-3K39V-2T3HJ-93F3Q-GT.

April 3rd 2017
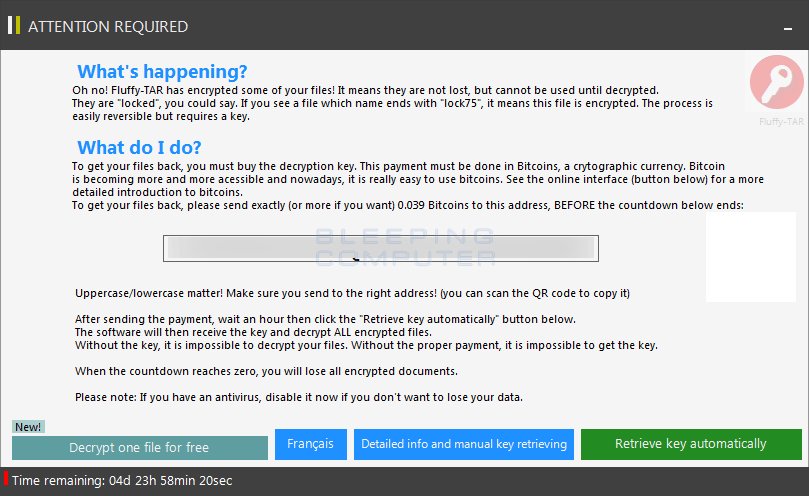
Fluffy-Tar Ransomware Discovered
BleepingComputer discovered the new Fluffy-Tar Ransomware. Currently in-dev, but sports a cute mascot, supports French and English, and comes with a TOR site.
Cerber Changes Ransom Note File Name
MalwareHunterTeam noticed that Cerber changed the ransom note file name to _READ_THI$_FILE_%random%_(hta|jpeg|txt).
Amadeous Ransomware Continues to be developer
MalwareHunterTeam found a new variant of a ransomware that has been named Amadeous.
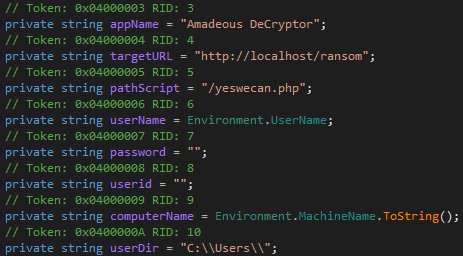
New HiddenTear Faizal Ransomware
BleepingComputer discovered that someone named "Faizal" is playing with HiddenTear. The ransomware appends the .gembok extension to encrypted files.
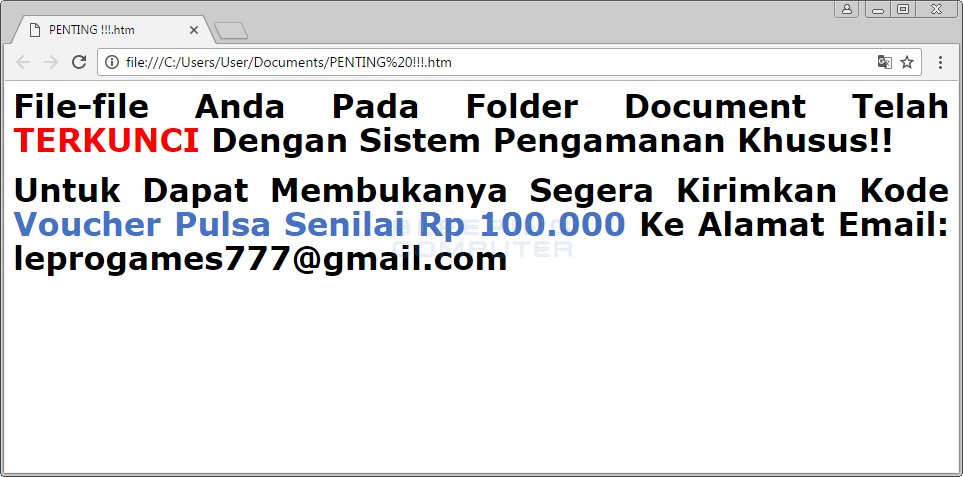
April 4th 2017
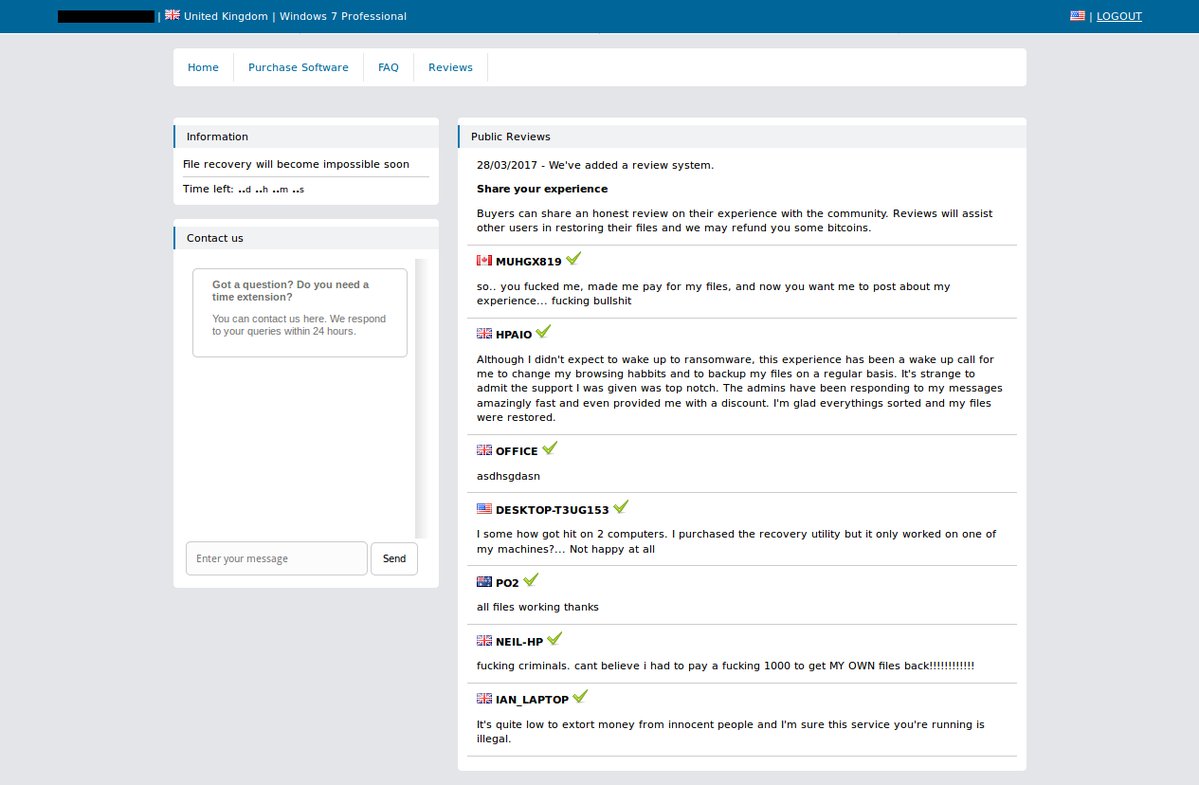
PadCrypt's TOR Payment Site Gives Discounts for Good Reviews
MalwareHunterTeam noticed that PadCrypt's TOR site has been updated to include a review page where the devs state that a good review could lead to a refund of some bitcoins.
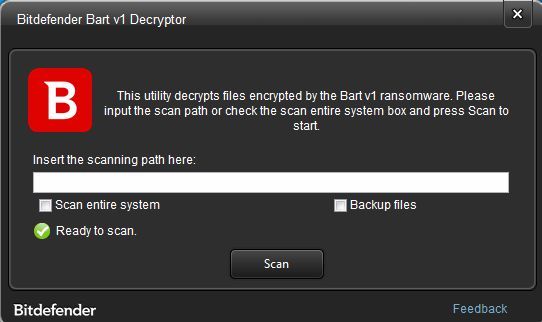
Bitdefender Releases a Decryptor for Bart Ransomware
Bitdefender releases a decryptor for the Bart Ransomware. One was already released a while back by Avast.
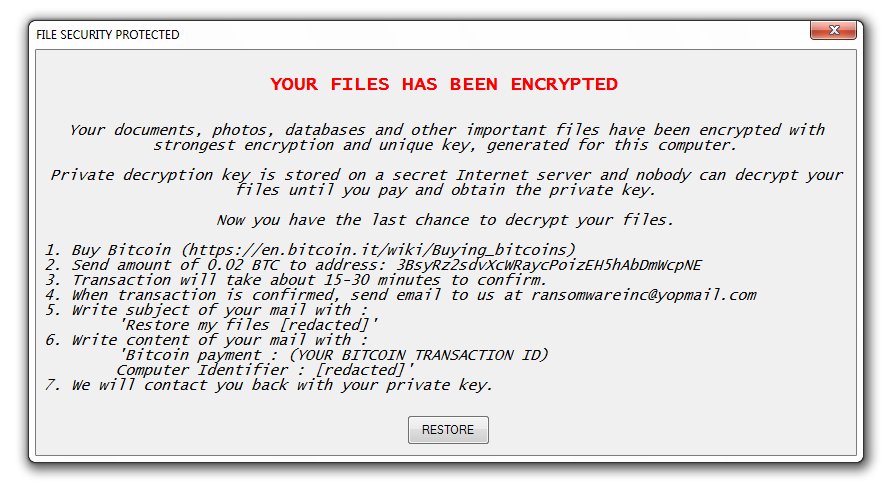
A new variant of the GX40 Ransomware Discovered
MalwareHunterTeam discovered a new variant of the GX40 Ransomware. Uses the email address ransomwareinc@yopmail.com.
New Jigsaw Ransomware Variant Discovered
Michael Gillespie discovered a new Jigsaw Ransomware variant discovered that appends the .I'WANT MONEY extension to encrypted files and then says to email ewsc77@mail2tor.com. Michael's decryptor updated to support this variant.
April 5th 2017
Vortex/Floreta Ransomware can be Decrypted
Michael Gillespie tweeted that anyone hit by Vortex / Floreta ransomware should contact him as he can decrypt the files.
New Samas Ransomware Variant Discovered
Michael Gillespie discovered a new Samas/SamSam ransomware variant that uses the extension .skjdthghh and drops a ransom note named 009-READ-FOR-DECCCC-FILESSS.html.
PadCrypt is now Version 3.5
MalwareHunterTeam found a sample of the PadCrypt ransomware that is now at version 3.5.
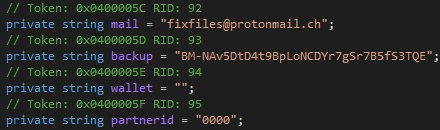
Fantom Ransomware Possibly Building a RaaS?
MalwareHunterTeam found a sample of the Fantom Ransomware that added a new partnernid variable. Could they be building a RaaS?
New CryptoWire Variant Released
MalwareHunterTeam discovered a new variant of CryptoWire that uses realfs0ciety@sigaint.org.fs0ciety as its name. Bizarre.
New In-Dev Python Ransomware Discovered
Karsten Hahn discovered a new in-development ransomware written in Python.
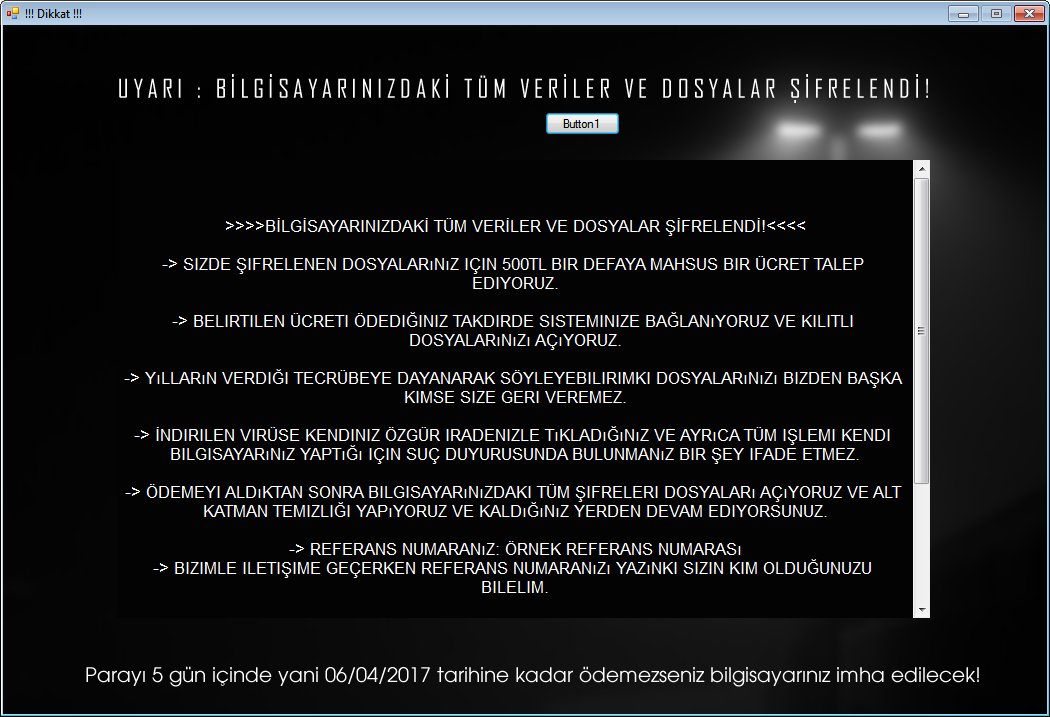
New HiddenTear Ransomware called Kripto
Karsten Hahn discovered a new Turkish HiddenTear variant called Dikkat. This ransomware is x64 only.
April 6th 2017
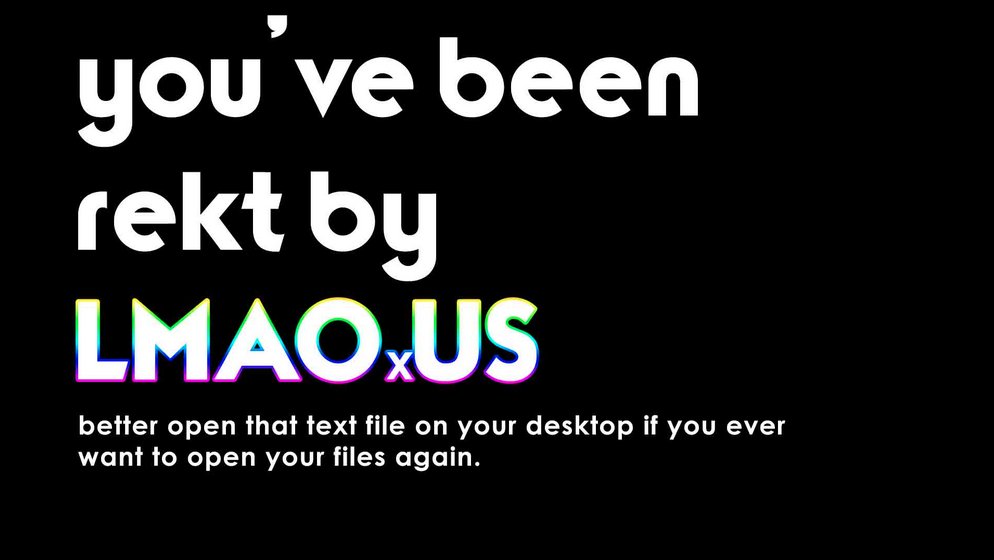
LMAOxUS Ransomware: Another Case of Weaponized Open Source Ransomware
An Indian developer is playing around with an open source ransomware builder, which in the long run may end up causing serious problems for innocent users. This developer, who goes by the nickname of Empinel and claims to be based in Mumbai, has forked the open source code of the EDA2 project, and with the help of another user, has removed the backdoor hidden in EDA2's original code.
This has already led to two Stolich variants being released and discovered by researchers MalwareHunterTeam & Jack.
Teenager Arrested in Austria for Spreading Philadelphia Ransomware
Austrian police arrested a 19-year-old teenager from Linz for infecting the network of a local company with the Philadelphia ransomware. The incident in question took place last year and targeted an unnamed company based in Linz. The attacker locked the company's servers, including its production database. The attacker asked for $400 to unlock the company's systems, but the victim refused and instead recovered its data via older backups.
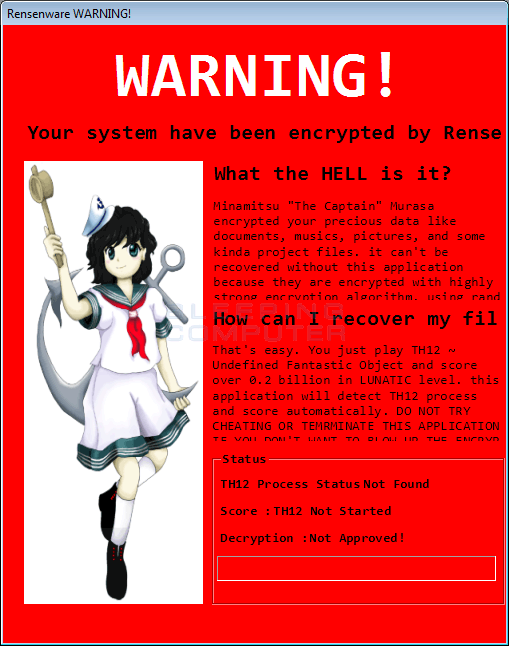
RensenWare Will Only Decrypt Files if Victim Scores .2 Billion in TH12 Game
A new ransomware called RensenWare was discovered today by MalwareHunterTeam that makes a unique ransom demand; score over 0.2 billion in the LUNATIC level of TH12 ~ Undefined Fantastic Object or kiss your files goodbye!
Ransomware Gang Made Over $100,000 by Exploiting Apache Struts Zero-Day
Both F5 Labs and SANS ISC released research detailing how for about the last month, at least ten groups of attackers have been compromising systems running applications built with Apache Struts and installing backdoors, DDoS bots, cryptocurrency miners, or ransomware, depending if the machine is running Linux or Windows.
Emsisoft Releases a Decryptor for the Cry9 Ransomware
Emsisoft CTO and Malware researcher Fabian Wosar released a free decrypter for the most recent strain from CryptON ransomware family, ‘Cry9.’ Victims can now decrypt files.. for free!
April 7th 2017
ClearEnergy - The "In The Wild" SCADA Ransomware Attacks That Never Existed
After the publication of an article in Security Affairs called "ClearEnergy ransomware aim to destroy process automation logics in critical infrastructure, SCADA and industrial control systems," security researchers used Twitter to bash CRITIFENCE for what they felt were lies about real world attacks, the company orchestrating a media stunt, and not releasing any research they could vet.
Matrix Ransomware Spreads to Other PCs Using Malicious Shortcuts
Brad Duncan, a Threat Intelligence Analyst for Palo Alto Networks Unit 42, has recently started seeing the EITest campaign use the RIG exploit kit to distribute the Matrix ransomware. While Matrix has been out for quite some time, it was never a major player in terms of wide spread distribution.
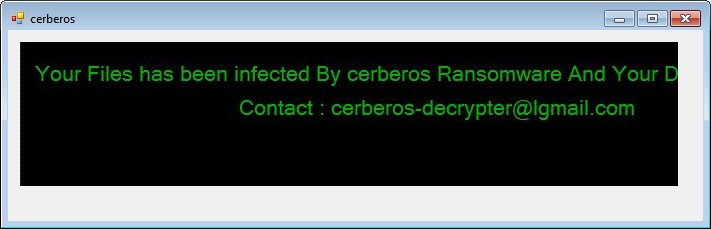
Cerberos Ransomware Discovered
Karsten Hahn discovered a new CyberSplitterVBS variant called Cerberos.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.











Comments
Amigo-A - 8 years ago
Many Thank!
With Your permission, I will supplement in the "Week Review" with information from my "Digest of Ransomwares", specially for those who can't track the detection of new incidents with Ransomwares every day, but want to be aware of new incidents, and inform his audience and subscribers, etc.
All descriptions in Russian, but General elements and "signatures" of Ransomwares have is in English and any other language. Besides, I hope that the Google's translation technology let it helps you understand the rest of the content.
This is not the final descriptions, I regularly add information. You can consult and refer as necessary and supplement me. Thank your.
Salsa Ransomware
http://id-ransomware.blogspot.ru/2017/04/salsa-ransomware.html
Rijndael Ransomware by already known humanpuff69
http://id-ransomware.blogspot.ru/2017/04/rijndael-ransomware.html
FinalRansomware Ransomware - this is new version of GX40 or based GX40, - presented above, but no name.
http://id-ransomware.blogspot.ru/2017/04/finalransomware.html
FakeWU or Fake WindowsUpdater Ransomware - this is new version of GX40 or based GX40, presented above, but no name.
http://id-ransomware.blogspot.ru/2017/04/fake-windowsupdater-ransomware.html
Zixer2 Ransomware
http://id-ransomware.blogspot.ru/2017/04/zixer2-ransomware.html
One Ransomware with a ransom-note in Portuguese 'Recupere seus arquivos aqui.txt'
http://id-ransomware.blogspot.ru/2017/04/one-ransomware.html
Kripto64 or Turkish HTx64 Ransomware - presented above, but no name
http://id-ransomware.blogspot.ru/2017/04/kripto64-turkish-ransomware.html
Kampret Ransomware
http://id-ransomware.blogspot.ru/2017/04/kampret-ransomware.html
Lawrence Abrams - 8 years ago
Amigo-A, you do realize that I have 3-4 of the ones listed in your comment in my article already ?
Amigo-A - 8 years ago
Yes, I same marker them in list, according to the files provided by colleagues.
This is a two new version of GX40 or based GX40. And Kripto64 or Turkish HTx64 Ransomware - presented above, but as Dikkat...
Amigo-A - 8 years ago
Dikkat - it's not named, it's "Attention !!!" in English. The name is indicated by the developer on the file submitted for analysis - Kripto.
Amigo-A - 8 years ago
Please fix Ceberos on Cerberos, as it is in the screenshot. Thank You.
Amigo-A - 8 years ago
I just want to be objective to add the information we've been able to find together (jointly and separately). All right, have a good weekend.