
The OceanLotus advanced persistent threat (APT) group (also known as APT32 or Cobalt Kitty) is using a steganography-based loader to drop backdoors on compromised systems.
According to the report published by the Cylance Research and Intelligence Team, OceanLotus uses the novel malware loader to load "a version of Denes backdoor (bearing similarities to the one described by ESET), and an updated version of Remy backdoor."
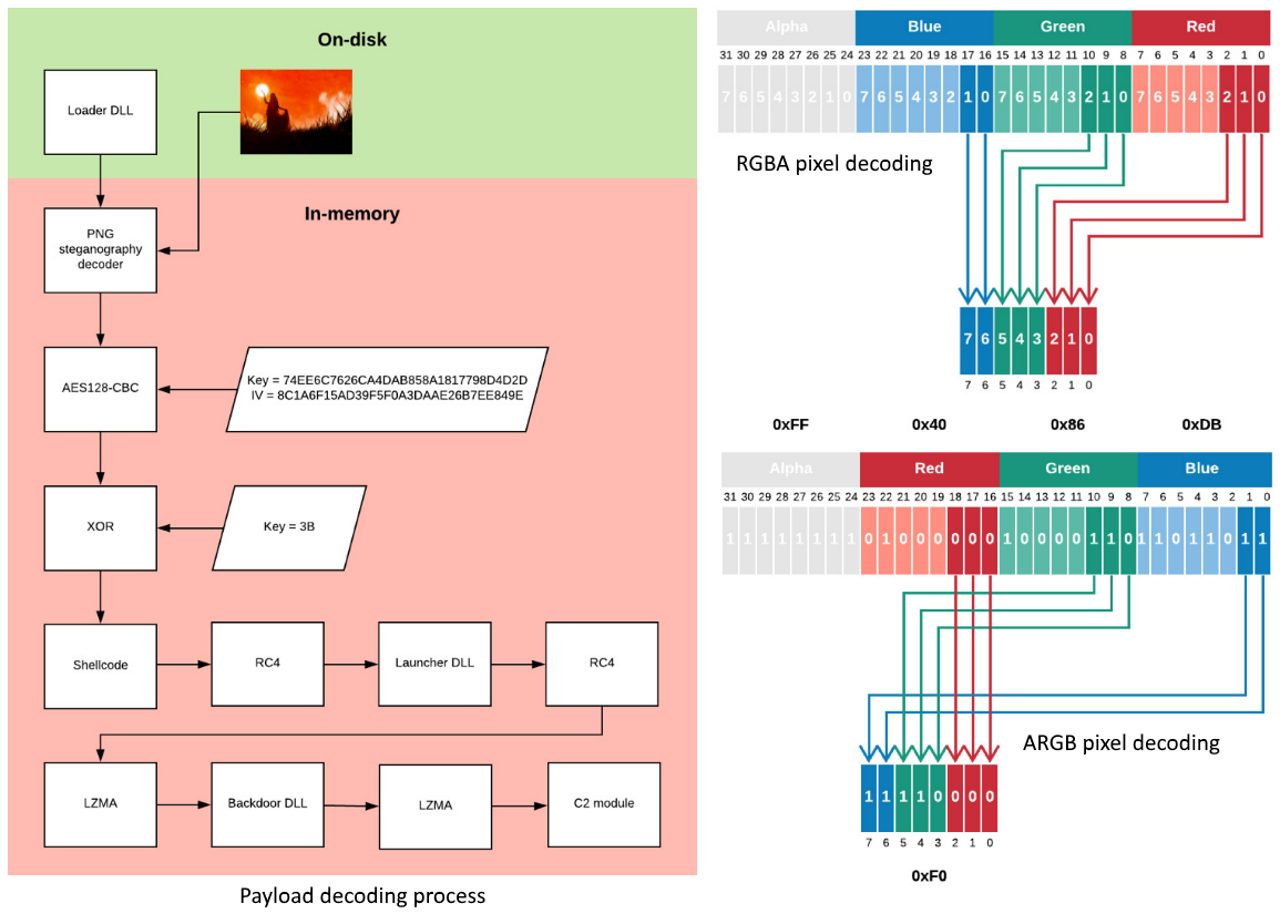
The steganography algorithm used by APT32 seems to be specifically developed for this purpose and it is designed to conceal the encrypted malware payload within PNG images to minimize as much as possible the possibility of detection by malware discovery tools.

The Cylance researchers observed the steganography loaders in the wild during September 2018 and discovered that, while their general architecture is not identical, the payload extraction procedure used by both of them is the same.
As further unearthed by Cylance's analysis of the two malware loaders, they both use side-loaded DLLs and an "AES128 implementation from Crypto++ library for payload decryption" as detailed in the feature comparison in the table below.
| Loader #1 Features | Loader #2 Features |
| Side-loaded DLL | Side-loaded DLL |
| Loads next-stage payload using custom .png steganography | Anti-debugging/anti-sandboxing check for parent process name |
| Uses AES128 implementation from Crypto++ library for payload decryption | Loads next-stage payload using custom .png steganography |
| Known to load Denes backdoor, might possibly be used also with other payloads | Uses AES128 implementation from Crypto++ library for payload decryption |
| Executes the payload by overwriting the return address on the stack | |
| Known to load an updated version of Remy backdoor |
While the two steganography-based malware loaders are used to drop backdoors on the targets' machines, "can be easily modified by the threat actor to deliver other malicious payloads. The complexity of the shellcode and loaders shows the group continues to invest heavily in development of bespoke tooling."
The backdoor loading process starts with the obfuscated loader payload being decoded, decrypted, and subsequently executed to load one of the two backdoors detected by the researchers.
To make malware analysis as cumbersome as possible, "the backdoor DLL and the C2 communication DLLs are heavily obfuscated using high quantities of junk code, which significantly inflates their size and makes both static analysis and debugging more difficult," says Cylance.
The C2 communication module is used to communicate via HTTP/HTTPS channels with the backdoor's command-and-control server and, as the researchers found out, it also comes with built-in proxy bypass functionality.
APT32 is a Vietnamese-backed advanced persistent threat group known to have targeted "foreign companies investing in Vietnam’s manufacturing, consumer products, consulting and hospitality sectors."
Multiple attacks targeting research institutes from around the world, media organizations, various human rights organizations, and even Chinese maritime construction firms have been attributed to this hacking group in the past. [1, 2, 3, 4, 5, 6, 7]
Just last week, some security experts think that APT32 might have been behind a security breach of multiple Toyota and Lexus sales subsidiaries leading to the personal information of roughly 3.1 million Toyota customers potentially being leaked.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.











Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now