BleepingComputer's ongoing coverage of whatever you want to call this thing (WanaCrypt0r, WannaCry, Wana Decrypt0r) can be found below. Many of these articles have been updated with new info as it has been discovered.
May 12th 2017 8:40 AM: Telefonica Tells Employees to Shut Down Computers Amid Massive Ransomware Outbreak
May 12th 2017 1:07 PM: Wana Decryptor Ransomware Using NSA Exploit Leaked by Shadow Brokers Is on a Rampage
May 12th 2017 5:24 PM: WannaCry / Wana Decryptor / WanaCrypt0r Info & Technical Nose Dive
May 13th 2017 4:14 AM: Wana Decryptor Ransomware Outbreak Temporarily Stopped By "Accidental Hero"
May 13th 2017 5:05 AM: Microsoft Releases Patch for Older Windows Versions to Protect Against Wana Decryptor
May 14th 2017 8:00 AM: Honeypot Server Gets Infected with WannaCry Ransomware 6 Times in 90 Minutes
May 14th 2017 9:00 PM: Microsoft Exec Blames WannaCry Ransomware on NSA Vulnerability Hoarding Program
May 15th 2017 2:01 AM: With the Success of WannaCry, Imitations are Quickly In Development
May 15th 2017 6:55 AM: WannaCry Ransomware Version With Second Kill Switch Detected and Shut Down
May 15th 2017 1:00 PM: Someone Created a WannaCry Version That Doesn't Use a Kill Switch
This is a dedicated help and support topic for the WannaCry, Wcry, WanaCrypt0r, and Wana Decrypt0r Ransomware. This ransomware is being spread very heavily today and I am sure we will be seeing a lof of victims.
This ransomware is currently being spread by the EternalBlue exploit. More info here:
Wana Decrypt0r Ransomware Using NSA Exploit Leaked by Shadow Brokers Is on a Rampage
First Variant: .wcry
Second Variant: .WCRY (+ .WCRYT for temp)
Third Varianmt: .WNCRY (+ .WNCRYT for temp)
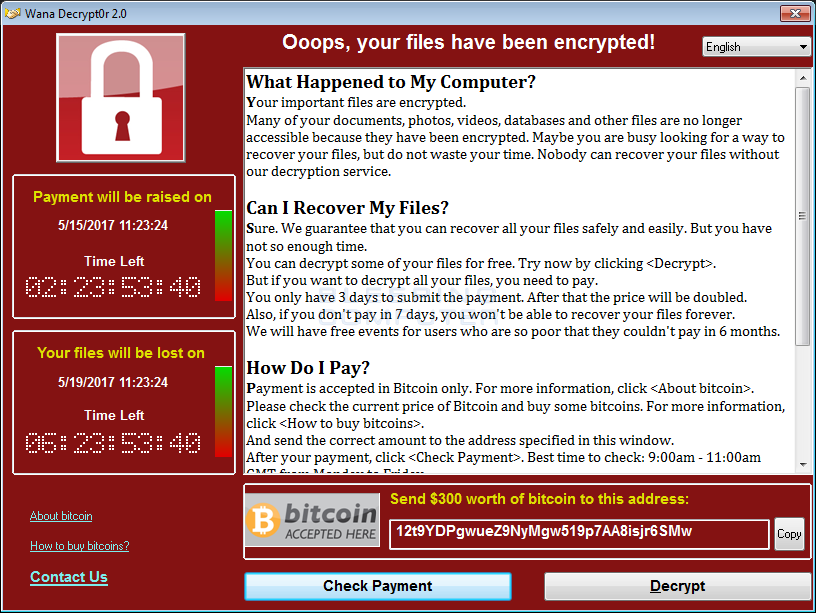
The ransomware will display a lock screen that contains the same information. This screen acts as the decryptor as well, but should be terminated as it will encrypt new files as it is running.
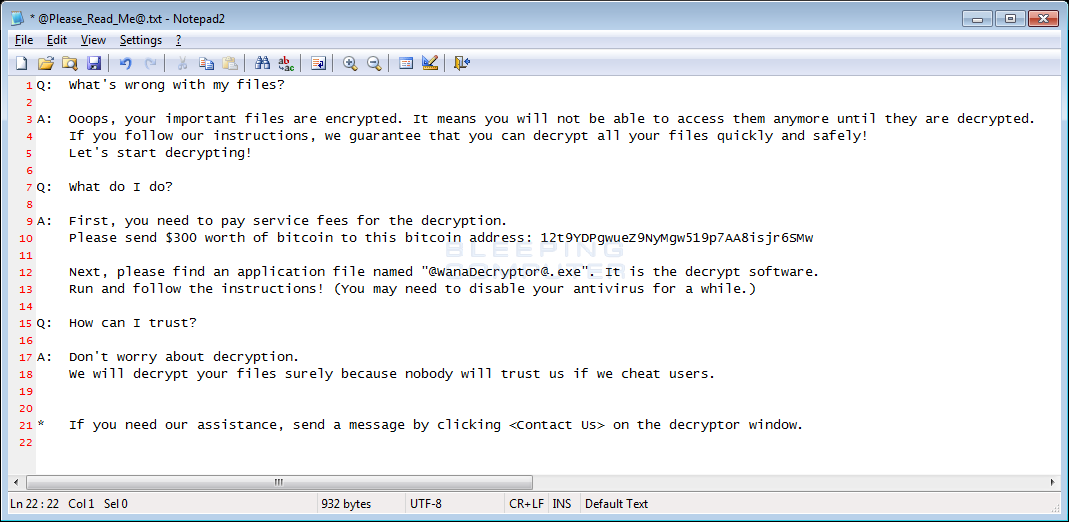
The ransomware will also drop a ransom note named @Please_Read_Me@.txt, which can be seen below.




 Back to top
Back to top